 We recently had to assist a customer in dealing with a phishing attack against an Office 365 user’s account.
We recently had to assist a customer in dealing with a phishing attack against an Office 365 user’s account.
What is Phishing?
Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising as a trustworthy entity in an electronic communication. Typically carried out by email spoofing or instant messaging, it often directs users to enter personal information at a fake website, the look and feel of which are identical to the legitimate site.
Phishing is an example of social engineering techniques being used to deceive users. Users are often lured by communications purporting to be from trusted parties such as social web sites, auction sites, banks, online payment processors or IT administrators.
Excerpt from Wikipedia (https://en.wikipedia.org/wiki/Phishing)
What Happened?
The user received an email requesting feedback on an email sent earlier. The user was distressed enough by the email to respond and apologize, whereupon the attackers sent a follow up email directing the user to a file to be downloaded.

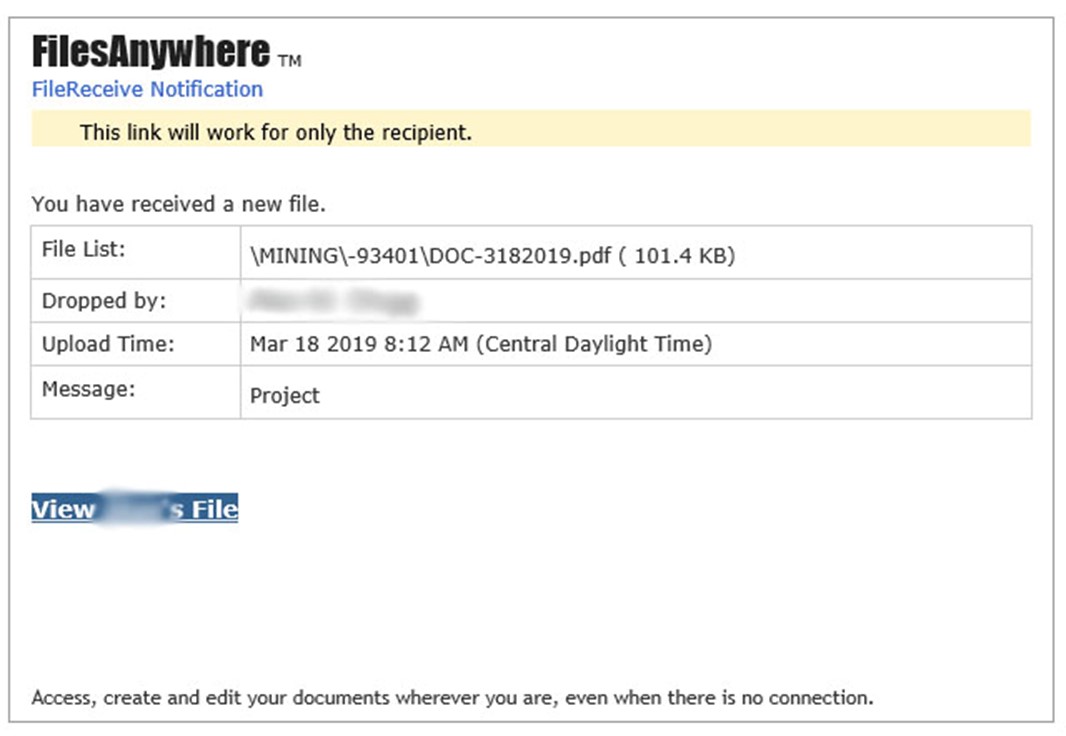 Clicking the link loads a login page, requesting the user’s Office 365 credentials, whereupon the user is directed to some documents. At this stage the documents don’t really matter, and if the user does not realise that they’ve entered their credentials into a bogus site, their account is wide open.
Clicking the link loads a login page, requesting the user’s Office 365 credentials, whereupon the user is directed to some documents. At this stage the documents don’t really matter, and if the user does not realise that they’ve entered their credentials into a bogus site, their account is wide open.
The attackers then take their time reviewing the user’s email inbox, to identify a plausible method of extracting a fraudulent invoice for payment.
When they are ready to act, they enable a forwarding rule on the user’s Inbox, directing all emails to an external email address, in order to respond to any queries and send the invoice for processing. It seems they target approximately $5k – $10k, probably to remain under the compliance and authorization radar. They then trigger a mass email from the user’s inbox, to spread their attack to as many contacts in the user’s mail account as possible prior to the Office 365 SPAM rules shutting the mailbox down. Finally, the attackers tend to delete as many emails as is easy to get to, in order to wipe out the traces of their intent. They do a hard delete, which means the email goes straight to jail, and does not first stop in the Deleted Items folder.
How do you know you’ve been caught? The first real indication is the forwarding rule which triggers a “Low-Severity Alert” on Office 365 to Administrators. Other indicators are if the user’s Inbox starts behaving strangely, or access to the Inbox becomes erratic. Also watch out for new rules being created.
What should you do when your email account has been compromised? There are some excellent articles posted by Microsoft, which can be found here (https://docs.microsoft.com/en-us/office365/securitycompliance/responding-to-a-compromised-email-account), on how to respond and what to do next.
How did we respond?
- Reset the User’s Password
- Block the User’s Account
- Remove any Administrative Roles the User may have on Office 365
- Disable the mail forwarding rule via Outlook Web Access (the forwarder does not seem to come up in either the Exchange Management Console or the local Outlook client)
- Disable any suspicious rules in the Outlook Client (We disabled them to allow us to interrogate them in more detail as part of the post mortem)
-
Run PowerShell script to check the audit logs, and attempt to create a timeline of events
- See here for the PowerShell syntax – https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-audit/search-mailboxauditlog?view=exchange-ps
- And here for an excellent implementation (Although it’s a bit outdated – based on Exchange 2010/2013) – https://gallery.technet.microsoft.com/scriptcenter/Generate-a-Report-of-a33cde56
- See here for the PowerShell syntax – https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-audit/search-mailboxauditlog?view=exchange-ps
-
If email entries were deleted, restore any recoverable items using the Restore-RecoverableItems PowerShell commandlet
- Once the emails have been restored and operational control of the mailbox returned to the correct user, you can reset the password and enable the account
What can be done?
To avoid phishing attacks in the future, it is highly recommended enabling Multi-Factor Authentication for all users. Additionally, it would also be useful to customize the Office 365 login page, so that users will more easily identify phony login pages.
In addition to these physical measures, it is important that users are made aware of the dangers of phishing and trained on how to spot phony or suspicious links and pages. Phishing is a social engineering attack and it relies on the resemblance to a credible source to solicit the user’s details.
The instances and successes of Phishing has certainly increased over the last period, with numerous reports received by Azuro, and even reported on in the news. Be alert.
Other helpful links:
- Connecting to Exchange Online via PowerShell – https://docs.microsoft.com/en-us/powershell/exchange/exchange-online/connect-to-exchange-online-powershell/connect-to-exchange-online-powershell?view=exchange-ps
- Office 365 Security Incident Response – https://docs.microsoft.com/en-us/office365/securitycompliance/office365-security-incident-response-overview
- Security best practices for Office 365 – https://docs.microsoft.com/en-us/office365/securitycompliance/security-best-practices?redirectSourcePath=%252farticle%252fSecurity-best-practices-for-Office-365-9295e396-e53d-49b9-ae9b-0b5828cdedc3
- Manage mailbox Auditing – https://docs.microsoft.com/en-us/office365/securitycompliance/enable-mailbox-auditing?redirectSourcePath=%252fen-us%252farticle%252fEnable-mailbox-auditing-in-Office-365-aaca8987-5b62-458b-9882-c28476a66918
